Last November I posted about an email response by John Callas, CEO of PGP, trying to dispel the perception that a government agency might have the computing power to break 128-bit keys. People seemed concern that while breaking 128-bit keys is beyond the resources of most people or groups, governments agencies still had a good shot. He thought this extremely paranoid, using the example of a computing cluster that enveloped the entire earth to a height of one metre high would still require 1,000 years on average to recover a 128-bit key.
I just put up on Scribd a 2008 whitepaper from Seagate that discusses their reasoning for choosing AES-128 over AES-256 for hard disk encryption. The whitepaper states that
- NIST has concluded and recommended that all three key-lengths (128-bit, 192-bit and 256-bit) of AES provide adequate encryption until beyond calendar year 2031.
- NIST’s recommendation above includes the threat model not only of predicting the key, but also of cracking the encryption algorithm. The difference between cracking AES-128 algorithm and AES-256 algorithm is considered minimal. Whatever breakthrough might crack 128-bit will probably also crack 256-bit.
Further, Seagate wanted to maximize the success of its solution by considering the additional business-side concerns:
- Must promote compliance with laws controlling export from the U.S. and import to other nations
- Must be cost-optimized
- Must be able to meet the needs of ALL target markets
AES-128 is sufficient or exceeds all the above criteria.
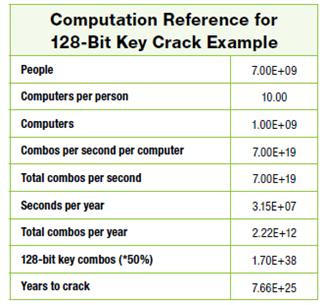
They also went on to discuss the computational task of recovering 128-bit keys, where assuming
- Every person on the planet owns 10 computers
- There are 7 billion people on the planet.
- Each of these computers can test 1 billion key combinations per second.
- On average, you can crack the key after testing
50 percent of the possibilities.
it follows that the earth’s population can crack one encryption key in 77,000,000,00,000,000,000,000,000 years! The graphic form of the argument looks like
Nonetheless AES-256 is being widely deployed since it conveniently lies at the intersection of good marketing and pragmatic security. In upgrading from AES-128 to AES-256 vendors can legitimately claim that their products use maximum strength cryptography, and key lengths can be doubled (thus squaring the effort for brute force attacks) for a modest 40% performance hit.



8 comments:
Doesn't Rainbow Tables = 0wned?
I personally think that for the most part, 128 bit encryption is more than sufficient for most sites. However, as technology advances, it is expected that at some point the industry standard will have to shift to 256 bit SSL Certificates encryption. I have decided to plump for 256bit encryption as these are all reasonably priced now - SSL247.co.uk and my customers have the added security now too.
Your calculations are incorrect!
If you can test 10 combos in a second, then you can test 600 combos every minute (10 x 60s).
So, if you can test 7.00E+19 combos per second, then you can test (7.00E+19 x 3.15E+7) = 2.21E+27 combos per year.
Which results in 77 billion years to crack a 128bit key on average.
Thanks for sharing your idea I always read your blog.
Laby[male suit]
Uneducated Security said...
Doesn't Rainbow Tables = 0wned?
April 14, 2010 11:16 AM
No. Rainbow tables have their limits. Salted hashes= rainbow tables owned
but also the word list for rainbow tables get massive the longer you allow them to go. I've never seen a rainbow table that goes past 11 characters long and that's if you're only using
A-Z, a-z, and 0-9. Not even getting close to special characters and spaces.
It's just as unrealistic for rainbow tables to be big enough to own aes-256 as it is for a brute-force attack to figure out a long enough password.
Which, if it were 64 characters long would take an insanely long amount of time.
No one has 64 character passwords though. It's burdensome and unnecessary.
Ouch, disproved by NSA. AES-128 has been cracked and it's only 2013, three years after this article. How about AES-256? Give them a couple more years and that will be cracked also.
Ouch, disproved by NSA. AES-128 has been cracked and it's only 2013, three years after this article. How about AES-256? Give them a couple more years and that will be cracked also.
The technical detail provided in this post is confusing for me to understand. I am looking for a simple detail so that I can learn the basic meaning and use of aes.
digital signatures
Post a Comment